Time:2023-12-23 Click:268

"If you see something nine hundred and ninety-nine times, you are perfectly safe; if you see it a thousand times, you are in terrible danger of seeing it for the first time." - G.K. Chesterton
1. How to solve your own problems
No matter your blockchain netizenship, we all love watching a masterclass cooking show where the ingredients may be at odds with each other in taste, but when together they maximize each other’s pleasing flavors and neutralize each other’s unpleasantness The aspect, like a musical composer, is that the high notes lead to the low notes, creating a symphony of taste buds that is a richness.

For blockchain network enthusiasts, hashing is a particularly interesting dish to imagine, and you can make hashing out of just about anything — no recipe required, that’s the whole point, debating what the best ingredients for hashing really are Foolishly, you use what you have, and given the range of ingredients you have - if you're competent enough - you can probably tweak the ingredients of a meal pretty well and make a delicious meal.
You can err on the side of caution and do what the majority thinks is best, but people are willing to take risks to find the truth, and to discuss an issue is to discuss it thoroughly, to introduce different perspectives and possibilities for solutions, and to find -- not just A solution – but a meta-solution that transcends previous goals.
Although Vitalik Buterin, the inventor of Ethereum, is the founder of a major Bitcoin publication, and Dominic Williams, CEO of Dfinity, also started researching the Ethereum community, the Bitcoin, Ethereum and ICP communities treat it in an acceptable way Thinking about each other, the way everyone eats together today seems too far-fetched for reality.
It seems like we should all have a good discussion about what our ingredients are? Let's see, the fate of the Metaverse depends on us.
What exactly are we trying to figure out? We are trying to explore how people will come to agreement in the future, and it is worth discussing that smart contracts on open distributed computing systems will provide higher certainty for agreements than traditional contracts using pen and paper and commitment systems. So, we should How to create a distributed computing system that works for everyone?
To clarify the issue, we must address the existence of schemes in distributed computing systems such as blockchain that act as a consensus mechanism (a way for computers in the network to come to an agreement) and as a sybil resistance mechanism (a way to limit the membership of computers in the network). way), in order to function reliably, the consensus mechanism relies on a Sybil resistance mechanism to limit the number of participants allowed into the system.
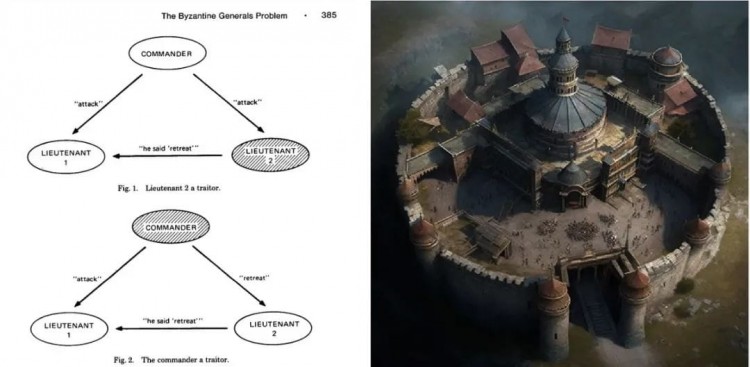
"In a distributed system, the failure of a computer that you don't even know exists can render your own computer unusable." - Leslie Lamport
The consensus mechanism helps individual participants agree on a certain function, such as the order of transactions initiated by the participants. If you change the order of transactions without an agreement, an attack called a double-spend attack occurs, sending to a specific address The same token is sent again to a different address, which breaks the functionality of the shared transaction ledger.
All consensus protocols have fault bounds, they are guaranteed to work properly in the presence of faults, which could be participants in the network acting as offline nodes or malicious nodes. As long as the consensus protocol is within its fault bounds, it will function as expected. , if the number of faulty nodes exceeds the protocol's fault bound, then an attacker may cause the protocol to stop its intended functionality.

“The 3E’s of Sybil resistance are entry costs, existence costs, and exit penalties.” - Dominic Williams
A witch resistance mechanism is needed to prevent an adversary from creating multiple failure nodes to overcome the failure boundary. The name of this attack was inspired by a novel written by Flora Rheta Schrieber about a woman with dissociative identity disorder. is a mental illness in which multiple different identities within the sufferer's psyche disrupt their cognitive functioning, much like multiple instances of faulty nodes disrupt the consensus functionality of a distributed system.
Dominic Williams proposes a structured approach to analyzing the effective dimensions of Sybil resistance mechanisms in The 3E Concept of Sybil Resistance: Entry Costs, Existence Costs, and Exit Penalties.
The entry cost is the resource cost requirement incurred in order to initially participate in the consensus protocol. In addition to the monetary cost, time and energy are also considered to be part of the resource cost.
The existence cost is the resource cost requirement to maintain continued participation in the consensus protocol. This cost requirement prevents participants from constantly investing in new identities and provides a more decentralized influence on the network because participants are affected by what they can support. Limit on the number of identities.
Exit penalty is the consequence of a network participant being kicked out of the network due to misbehavior. This requirement faces an adversary that may have unlimited attack costs. The attacker should not be able to recycle the resource cost of the attack to another instance and Infinitely updated attacks.
Now that we have a framework for understanding how protocols between computers form, we can now ask how Bitcoin, Ethereum, and the Internet computer protocol network resolve themselves.
2. Bitcoin uses proof-of-work for hash calculations

“A nice property of proof of work is that it can be forwarded through an untrusted middleman, we don’t have to worry about the communication chain of custody, it doesn’t matter who tells you the longest chain, the proof of work speaks for itself. ." -Satoshi Nakamoto
Bitcoin is a simple protocol optimized to do only one thing: act as an append-only transaction ledger to move value over the internet, its invention was a reaction to changes in monetary policy imposed by governments and enforced by banks, created by Satoshi Nakamoto Bitcoin proposes both a cryptoeconomic consensus mechanism and a Witch Resistance mechanism, which is the proof of work.
At its core, Proof of Work is a competition where, in order to add a new block of transactions to the ledger, a miner must find a "Nonce" value that will produce a block whose hash of that transaction starts with a certain number of leading zeros. .
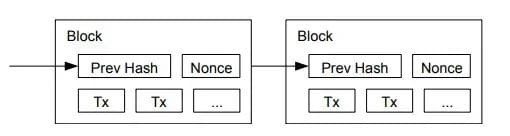
A block in the Bitcoin protocol is a data structure that contains many data fields. Miners are not allowed to change these data fields except for a certain value. These data fields are called "Nonce", abbreviation: number is used only once, and miners change the nonce. Hashes are generated using the SHA-256 algorithm until a hash is generated that meets the difficulty target.
Bitcoin's network difficulty is adjusted based on computing power by adding or subtracting a leading number of zeros to the target hash value to reduce or increase the probability that a miner will successfully meet the difficulty requirement.
The hash generated by the SHA-256 algorithm is a random and unpredictable value. There is no shortcut to finding a random number suitable for the target hash. The participating miners must rotate the random number, by consuming energy, trying different values until a match is found. hash, and the winner is granted the ability to add a block to the Bitcoin ledger, including the block reward.
Sybil resistance occurs because in order to find a matching hash, you have to drain computing power through electricity in order to find the combination that enables you to append a block and receive the block reward.
Since the relative proportion of block rewards received by a miner is directly proportional to the number of hashes produced by the miner, it is up to the game to perform this hashing as efficiently as possible. For hardware, you need an ASIC (Application Specific Integrated Circuit) dedicated to hash mining. ), for energy, you need a cost-effective power supply to power your hardware.
The entry cost of Witch Resistance will be the purchase of these ASIC hardware and miners, the existence cost is the huge electricity cost required to power the ASIC hardware, and the exit penalty is the premium lost when selling the ASIC miner, which is a relatively weak penalty.
Theoretically, an adversary that disrupts the Bitcoin network by overcoming the failure boundary would need to secure ASIC hardware and cost-effective energy sources to generate 51% of the hash power currently generated by the Bitcoin network, so spawning camps An attack could render the proof-of-work blockchain useless.
When you get a hash from a SHA-256 of some input bytes, the output is random and unpredictable, so the hash is a random number generator, and it is recognized that stateful decentralized networks are Satoshi Nakamoto's innovations in public cryptoeconomic consensus, powered by random numbers, led to other forms of decentralized network security.
3. Ethereum uses proof of stake for hash calculations

“So the one-line philosophy of proof-of-stake is not that security comes from burning energy, but that security comes from financially losing value.” - Vitalik Buterin
Ethereum is a platform built for hosting a new type of software called “smart contracts.” Similar to a vending machine, a smart contract is defined by a predetermined input that produces a predetermined output in an autonomous manner. implement.
While Bitcoin is arguably a protocol smart contract, the Ethereum protocol provides Turing-complete programmable smart contracts using a language called "Solidity" as a more flexible way of defining the specific inputs and outputs of a digital protocol. Way.
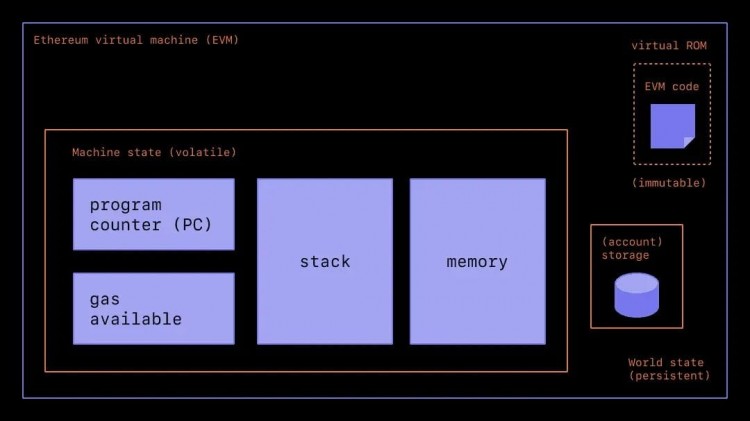
The Ethereum Virtual Machine (EVM) is the environment in which smart contracts live. The Ethereum protocol retains only a canonical state that is shared by all nodes in the network. If Bitcoin acts as a transaction ledger, Ethereum acts as the state machine of the Internet. The "Turing completeness" of a state machine means that given enough time and resources, it can be used to solve any computational problem.
Decentralized finance (DeFi) applications that support trading, lending, stablecoins, derivatives, and other uses are possible, as well as other applications such as NFTs and DAOs, and Ethereum has the potential to serve as a global settlement layer for DeFi transactions.
Ethereum initially used Proof-of-Work as its consensus algorithm, but due to the cost of maintaining and protecting the protocol's original configuration, after years of research and development, Ethereum moved to Proof-of-Stake, a consensus mechanism, and a Sybil-resistant mechanism during the "merger" The coupling between them is reduced, allowing them to be optimized independently.
The current consensus mechanism of Ethereum is named "Gasper", which is a combination of Casper FFG and LMD-GHOST consensus rules. LMD-GHOST is used to determine the legal state of the blockchain by confirming the block with the most calculations and latest messages. Casper FFG is used to finalize confirmed blocks to achieve tamper-proof permanence of blockchain consensus.
The Proof-of-Stake Sybil Resistance mechanism is a scheme in which network nodes (called validators) participate in Sybil Resistance by staking a predetermined number of tokens (32 Ethereum) and then, if the node follows the consensus rules, the amount locked Proportionately receive token rewards, and nodes that violate consensus rules will be “slashed,” causing them to lose their staked tokens.
"Verifiers" are virtual entities in proof of stake, replacing "miners" in proof of work. Verifiers are responsible for storing data, processing transactions, and adding blocks to the Ethereum blockchain. In the absence of randomness generated by proof of work, In the case of hashing, validators in proof-of-stake rely on an algorithm called RANDAO (Randomized Decentralized Autonomous Organization) to pseudo-randomly select validators to propose appending a block to the blockchain in a fair and verifiable manner. middle.
Sybil Resistance for Ethereum Proof-of-Stake The cost of entry will be the capital required to purchase the Ether required to run a validator node, the cost of existence is the cost of the bandwidth required to maintain validator node instances, which is a relatively weak cost, exit Penalties have cases defined in terms of LMD-GHOST and Casper FFG consensus.
"Slashing" occurs when a validator violates specific rules in the Ethereum protocol, which may be part of an attack on the chain or "Byzantine behavior." Slash conditions associated with Casper FFG are imposed on the finality of restored blocks. attack costs, while the slashing conditions associated with LMD-GHOST impose costs on "no-stake attacks" and "balanced attacks", for both types of slashing Byzantine attackers are imposed unlimited attack costs.
Although Proof-of-Stake has advantages over Proof-of-Work, there are also some inherent challenges. Since validators are virtual instances and do not require dedicated ASIC hardware, network nodes can be cost-effectively created on enterprises like Amazon Web Services. For such cloud services, it is possible for the cloud service provider to interfere with the validator or shut down the validator.
Another issue is that using traditional short selling methods and acquiring a large amount of Ethereum, it may be possible to perform a "short attack" on the proof of stake system. A sybil attack against the proof of stake will also occur immediately, because the adversary does not have to spend time configuring any hardware to Launch an attack.
Between Proof-of-Work and Proof-of-Stake, which Sybil-resistant mechanism is superior is debatable, but is it better to have both since they are both highly resistant to different types of attacks? If so, other considerations may be raised.
4. ICP uses proof of useful work to hash itself

“Proof-of-useful work creates a sovereign blockchain network hosted by specialized hardware, and combined with deterministic decentralization and special cryptography, it can create horizontally scalable, secure public blockchains with extraordinary efficiency.” - Dominic Williams
The Internet Computer Protocol (ICP) was designed to serve as the world computer for the Internet, and its goal is to replace traditional IT stacks with decentralized cloud infrastructure (developers may be in danger of falling into the platform risks that exist on enterprise cloud infrastructure), ICP works by leveraging dedicated nodes run by independent data centers that use ICP to send messages and collaborate to form a virtual global computer.
Nodes in the subnet are managed by a high-level DAO called the Network Nervous System (NNS). The subnet then hosts smart contract code packages called "containers", which are the building blocks of dApps hosted on ICP. Code is compiled into Wasm from every possible language, including ICP's own native language "Motoko," and in order to orchestrate the execution of the container code and verify the network status of the nodes, a set of keys called "chain key cryptography" are used.
Dominic Williams seeks to create faster blockchains by repurposing traditional Byzantine Fault Tolerance (BFT) consensus mechanisms to enable a decentralized environment.
The consensus algorithm has security and liveness to measure its effectiveness. Security means that nothing bad will happen, and liveness means that good things will eventually happen. The traditional BFT protocol relies on multiple rounds of message passing to provide Instant security.
There are three different types of Byzantine Fault Tolerance protocols:
The synchronous BFT protocol assumes that all messages are delivered within a certain time and that all participants know how long the message will take to be delivered. When the network asynchrony is high enough (such as during a Ddos attack), the synchronous protocol becomes insecure and cannot Output value, although the Bitcoin Satoshi consensus is never directly described in the white paper, it can be classified into this category.
The partially synchronous BFT protocol assumes that all messages are delivered within a certain time, and all participants do not know how long it will take to deliver the message. When the network asynchronousness is high, the partially synchronous protocol is still safe, but it cannot output values. Ethereum The Gasper consensus mechanism is unique in that it incorporates aspects of the synchronous protocol in LMD-GHOST, which sets strict timing conditions, and aspects of the partial synchronization protocol in Casper FFG, which relies on epochs for finalization decisions.
The asynchronous BFT protocol does not make any timing assumptions about network messages, so it is not susceptible to DDoS flat-line attacks. The asynchronous protocol relies on a random number generator to guide the messaging between participants. Dominic Williams concluded that generated by cryptography Eventually consistent, blockchain-like protocols powered by random numbers are superior in a decentralized environment.
The Dfinity Foundation, led by Dominic Williams, began using "threshold relays" to generate random numbers, thereby using BLS signatures to aggregate a source of randomness that is incorruptible, unmanipulable, and unpredictable without the use of a consensus mechanism, and then , this random beacon chain is used as a stepping stone to other forms of consensus.
ICP’s Witch Resistance Mechanism is called Proof of Useful Work, and Proof of Useful Work is not a competition of proof of work, but cooperation.
ICPs are created by hardware nodes similar to ASIC miners in Bitcoin, unlike validators in Ethereum, which can be created on virtual machines using enterprise cloud infrastructure. These are dedicated node machines that process transactions and calculations. .
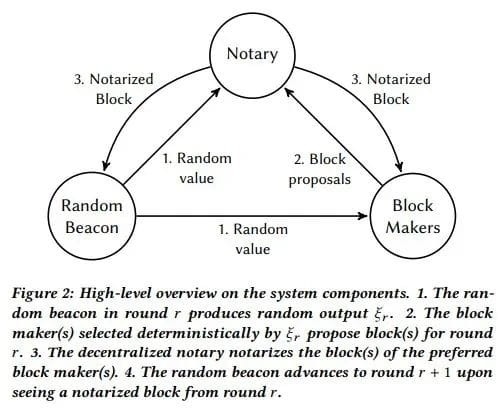
These node machines are grouped in so-called subnets and are incentivized to stay within a productivity range to produce the same number of blocks as other nodes in the subnet. A random beacon chain is used to select the ranked individual node as the leader, and Blocks are generated through a mechanism called Probabilistic Slot Protocol (PSP).
If that selected node fails to generate a block, the next node in the ranking has a chance to generate a block. Nodes built to the same standard specifications as other nodes in the subnet should be able to generate blocks when selected by a random beacon.
Since a random beacon determines which node can generate a block, a node built with higher specifications than the rest of the subnet will not have any advantage in receiving a higher level of reward than other nodes. When the network load is low, adopting Nodes built with lower specs may fail to generate blocks and receive lower reward levels than other nodes, or may even be slashed and deleted.
In this way, ICP networks protect nodes from statistical skew, and the chain-key encryption protocol enables ICP to add and remove nodes from the network in an elegant manner without interrupting its operations.
The Network Nervous System (NNS) is a key part of the ICP infrastructure and serves as the governance mechanism of the protocol. Instead of relying on social coordination from a foundation or company to organize protocol management, you have a DAO designed for on-chain governance, in which Votes are recorded on the blockchain ledger, and voting rules are transparent - predefined and communicated.
With protocol updates for on-chain DAOs embedded in the system code and implemented immediately upon approval, NNS DAO governance can account for special circumstances and prevent nodes from being curtailed for bona fide reasons that may occur through no fault of the node operator.
Voting in NNS involves users locking their tokens into so-called "neurons", which enable delegated voting using a follower system and a flexible weighted voting system where voters can choose to lock their tokens for how long and for as long as they choose. , the greater the voting power of their neurons, and staking rewards are then distributed to voting participants to incentivize value participation.
It is worth noting that while the NNS governance system may look similar to a proof-of-stake system, it is a governance mechanism rather than a consensus Sybil-resistant mechanism.
Although NNS can be called the most advanced DAO in the world, it can still make important upgrades by using a trusted execution environment of node hardware to improve network security and using People Parties as proof of personality to improve network security, which will benefit through Proven human voting mechanism.
The Sybil resistance mechanism of ICP useful work proof depends on the random beacon chain, probabilistic time slot protocol and NNS. All 3 E of resistance to Sybil attacks are achieved through useful work proof, and the entry cost must be added through NNS governance. The acquisition cost of the hardware node machines, the existence cost is the cost of hosting and running the hardware node machines so that they operate within the productivity of the subnet, the penalty for exiting the ICP includes a penalty guided by the NNS of the failed node to provide a higher environment Accuracy.
The purpose of ICP is to integrate with Bitcoin and Ethereum, both to benefit its own system and improve the system of its predecessor. Using new threshold cryptography designed by the Dfinity Foundation's team of cryptographers, containers in ICP can be used in Bitcoin and sign transactions on the Ethereum blockchain without using a central custodian (such as Chain Bridge) that could be exploited.
Integration with Bitcoin is already happening, Bitcoin integration on ICP can port smart contract functionality onto the Bitcoin network, enabling a DEX managed by a DAO, which can use Bitcoin to manage Bitcoin and other use cases such as SocialFi and GameFi , ICP will benefit from Bitcoin’s massive liquidity.
Ethereum can be enhanced by integrating with ICP. By offloading computationally intensive processes to ICP containers and then executing settlement logic on the Ethereum base chain in a manner similar to L2 aggregation, the scalability and security of interaction with the EVM can be improved. Working with efficiency and efficiency, the reverse Gas model on ICP means that the user interface of Ethereum dApps will become more efficient because users do not need to pay upfront to interact with Ethereum smart contracts.
DeFi applications on Ethereum are secure on the backend, but for users to interact with them, they must go through a vulnerable frontend built on an enterprise cloud provider. ICP and Ethereum integration will allow Ethereum dApps to use ICP to log into the Internet Identity authenticates users more securely, and ICP containers will be able to directly serve users on Ethereum dApp websites without using an enterprise cloud platform.
The integration can also use SNS infrastructure to form a fully autonomous DAO in Ethereum. As the ICP function develops, it is ultimately hoped to allow Ethereum validators to host their nodes on the ICP to solve the current platform risk issues faced by proof-of-stake participants. .
With tools like this in place, communities need to have the courage to understand the underlying protocols and build systems that support digital sovereignty, which will be sorely needed in the coming era.
5. Hash Metaverse
“It’s not a simple space, but the fact is, just like Ethereum adds value to Bitcoin, Internet computers can add huge value to Ethereum, and I believe that will continue to be true, and vice versa, Ethereum is important to the whole Ecosystems matter, including Internet computers, this is not a zero-sum game." - Dominic Williams
The act of eating together is a test of civilization. Imagine that all social agreements must succeed for you and your social network to share a feast. A feast is an act of sustaining and reciprocal altruism, as there is no guarantee that one, no matter how wealthy, Ability to always capture enough food to sustain one's life.
So when you can, it's prudent to express gratitude through the act of sharing and store the spoils of the day's hunt with your friends. In this abundance of sharing, you can achieve greater sustainability. Develop agreements that benefit both you and others, a win-win and help-win scenario.
Just like making a hash meal, where every carefully chosen ingredient added makes the meal more likely to be sustained, it is arguably preferable to have all three types of witch resistance in the network, Because each type is more powerful than the others, other attacks can be targeted against specific types of attacks, with the presence of each attack making the other attacks more powerful.
A common argument made by proponents against the concept of a Bitcoin consensus protocol is that the need for proof-of-work to consume energy is a waste of energy and therefore unsustainable. We know from developmental psychologists that iterative games to reach consensus are better than imposing Power is more sustainable, because imposing power is a waste of energy, imposing "my blockchain is better than yours" is a real waste of energy.
The word "hashing" is a key concept in these protocols. It is repeated with the word "hacking". Their concepts are also similar to some extent. Hacking is about using the full potential of the tool according to the intention. A hacker is a person who enjoys exploring the details of a programmable system and how to extend its capabilities, as opposed to most users, who prefer to learn only the minimum necessary knowledge.
In bringing Bitcoin, Ethereum, and ICP hashes together, we can enjoy exploring the details that extend their capabilities into a world network that we can all use to reach our full potential to solve individual challenges.
Blockchain networks are an ideal tool for achieving freedom and escaping tyranny because of their potential to solve fundamental organizational dilemmas in the human condition:
The kingmaker's dilemma is that trusted intermediaries tend to profit by acting as go-betweens to facilitate agreements. The more powerful the intermediary, the greater its leverage to capture value. The king is favored because in disputes without judicial mediation , must be resolved through diplomacy or war, the inherent decentralization characteristics of blockchain networks lead to determinism, enabling intermediary networks to eliminate the model of a single trusted middle party.
The Tower of Babel Dilemma is the tendency of organizational hierarchies to become more opaque as the hierarchy grows. The centralized leader at the top of the tower is less likely to consider the lower levels of the social organization. As the social organization grows, blocks The transparency inherent in the chain will alleviate the confusion caused by disjointed information.
The Return to Violence Dilemma refers to the tendency of a party with superior weapons to use violence to extract value from a less defensive party. Cryptography of digital asset control on the blockchain means that ownership can now be transformed into pure information, with cryptography as the defender. Provides advantages and adds cost to rubber hose attacks, thereby increasing friction on the scale of brute force attacks.
As with past technology cycles, we will witness a dramatic unbundling and rebundling of the way society operates, affecting the way people think and their quality of life, and we would do well to understand that negotiating with tyrants can only be achieved if sovereignty is achieved.
To achieve sovereignty, the basic trust layer of society must be increased so that people can cooperate on a large scale. The constraints on corporate and government power are property rights and decentralization. The network will be as meaningful as religion and country.
With this fact in mind, we can look forward to a future where we can sit side by side at a table and carefully discuss the bright future of the Metaverse while enjoying a hash feast we all made together.
"Computers can be used as tools to liberate and protect people, not to control them." - Hal Finney
IC content you care about
Technology Progress | Project Information | Global Events
Collect and follow IC Binance Channel
Stay up to date with the latest information